-
Procrastination via Optimization (Yak Shaving)
On the path to investigating static site generators for my blog, I ran into a seemingly endless series of optimization tasks. I installed 11ty, and the first thing I noticed is that my distro (Pop_OS!) has an outdated Node.js. That means I had to install NVM, (node version manager) to install and select the right…
-

Suddenly, a letter
I don’t know how often this phenomenon will happen in the future, but has a handwritten letter ever appeared out of the blue at exactly the right moment? It’s strange to contemplate that someone was thinking of you, wrote a letter, and in that cascade of events it appeared right when you needed it. My…
-

Should I switch to a static site generator?
Since 2002, this site has been running on WordPress or some other dynamic site, hand-crafted in one form or another. And it’s always been self-hosted or at least self-managed. I covered this already in 2020, but five more years have gone by and I’m nostalgic again, and thinking of another switch. Check out 18 Years…
-

An Open Letter to John Darnielle
I took an action item at lunch with friends to send this letter a few weeks back. I decided that finding John Darnielle’s address or email and then sending him this would sound too much like a request. And, walking by Merge Records to just drop it off would be super creepy. Instead I’ll just…
-

Bread Box Assembly
Yesterday Kat pulled out a bread box that had been hiding in our pantry since we moved downtown. Before that, it had been tucked away in our basement ever since I moved into Kat’s house. Long neglected, it still looked amazing sitting on the counter under the cabinet lighting. This made me think a lot…
-

2024 Summary
It’s been a while since I’ve posted. In fact, this is the first post of 2024. It’s been a whirlwind of a year. The year started out spending lots of time with friends and saying an untimely, final goodbye in January. Lots of memories and pictures were shared, drinks were had, and tears were shed.…
-
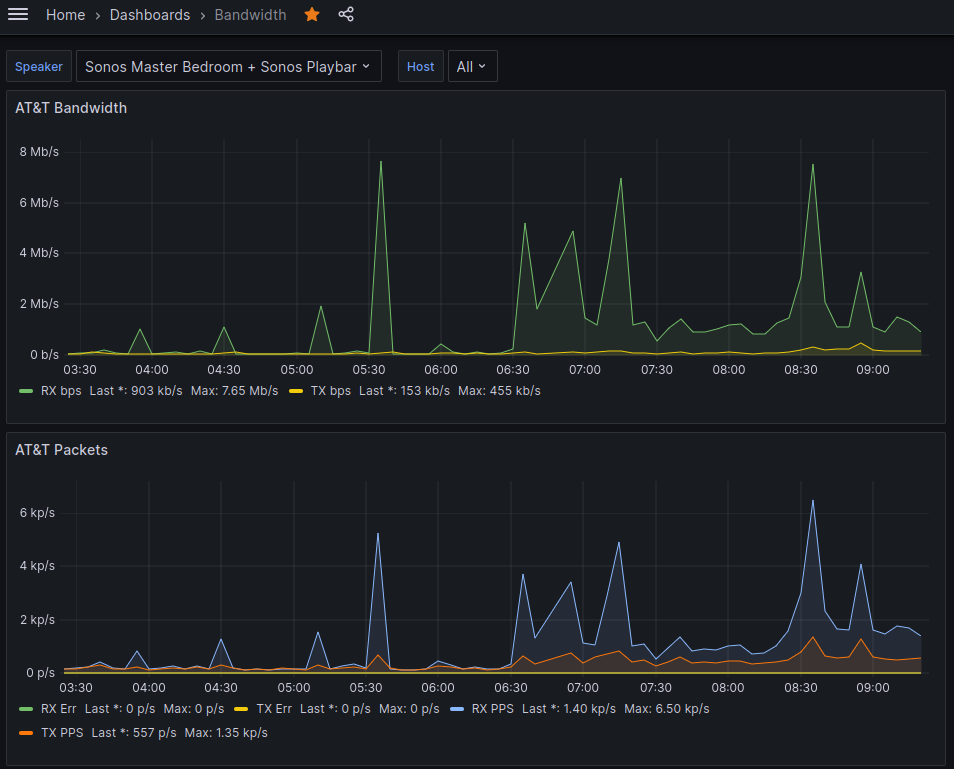
Measuring AT&T Internet Bandwidth with Python, InfluxDB, and Grafana
Any technical system you build inevitably slides into decay as the ecosystem you’ve borrowed from upgrades slowly over time while you’re off doing other things. The parts you custom tailored now no longer fit. Some of the suppliers go out of business. Some changed businesses altogether. That’s where I find myself with my home network…
-

A Deepness in the Sky
Here’s my review of A Deepness in the Sky by Vernor Vinge. I’m not leaving reviews on Goodreads anymore, but it felt like this deserved a mention somewhere publicly. Five stars. Highly recommended. Would read again. I picked up A Deepness in the Sky on a rainy day Oak Island friends beach trip after looking…
-

Cascais, PT
I tried surfing at Guincho Beach in Cascais, Portugal. I feel like I did a pretty terrible job, but Kat and Elly were awesome. The scenery and waves could not be beat!
-

Bernd das Brot
One of my favorite parts of visiting Germany is Bernd das Brot. Whenever you turn on the kids cartoon channel at night you can find Bernd hanging out grumbling about his situation. On this trip, he’s become AstroBrot, floating through space looking for peace and quiet, but constantly interrupted by satellites blaring phone calls and…